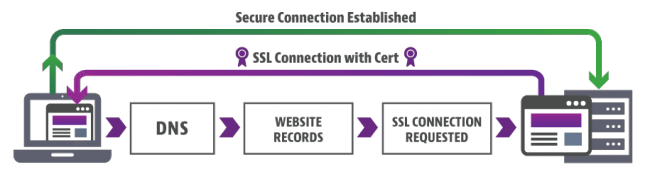
SSL is based on the mathematical intractability of resolving a large integer into its also-large prime factors. Using this, we can encrypt information using what’s called a “private-public key pair”. Certificate authorities can issue SSL certificates that verify the authenticity of such a secured connection, and on the same note, a self-signed certificate can be produced without third-party support. By the end of the tutorial, you will have a web server accessible via HTTPS using a self-signed certificate.
It is important to note that without proper certificate from a proper certificate authority, your browser will show warnings about the security of the site when viewed over HTTPS, even thought it is more secure than it was previously.
If creating a website in the real world and data security (especially payment details) is a concern, have a look at Let’s Encrypt – a free, automated, and open certificate authority brought to you by the non-profit Internet Security Research Group (ISRG).
Self-signed certificates are fine for use internally in your organisation, and once the user accepts the browser warning the first time, they shouldn’t see it again. So let’s begin.
We will carry out these followig steps on a Debian Linux server that we have already installed the apache2 and the sudo packages on to.
Enable the SSL Module
First, enable the Apache SSL module.
sudo a2enmod ssl
The default Apache website comes with a useful template for enabling SSL, so we will activate the default website now.
sudo a2ensite default-ssl
Restart Apache to put these changes into effect.
sudo service apache2 reload
Now it’s time to generate our cert.
Create a Self-Signed SSL Certificate
First, let’s create a new directory where we can store the private key and certificate.
sudo mkdir /etc/apache2/ssl
Next, we will request a new certificate and sign it. First, generate a new certificate and a private key to protect it.
- The days flag specifies how long the certificate should remain valid. With this example, the certificate will last for one year
- The keyout flag specifies the path to our generated key
- The out flag specifies the path to our generated certificate
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/apache2/ssl/apache.key -out /etc/apache2/ssl/apache.crt
Invoking this command will result in a series of prompts.
Common Name: Specify your server’s IP address or hostname. This field matters, since your certificate needs to match the domain (or IP address) for your website. Fill out all other fields at your own discretion.
Example answers are shown below.
You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ——- Country Name (2 letter code) [AU]:IE State or Province Name (full name) [Some-State]:Louth Locality Name (eg, city) []:Dundalk Organization Name (eg, company) [Internet Widgits Pty Ltd]:ITLC Organizational Unit Name (eg, section) []:DKIT Common Name (e.g. server FQDN or YOUR name) []:mysite.com Email Address []:info@mysite.com
Set the file permissions to protect your private key and certificate.
sudo chmod 600 /etc/apache2/ssl/*
Your certificate and the private key that protects it are now ready for Apache to use!
Configure Apache to Use SSL
After making these change, our server will begin serving HTTPS instead of HTTP requests for the default site.
Open the server configuration file using nano or your favorite text editor.
sudo nano /etc/apache2/sites-enabled/default-ssl.conf
Locate the section that begins with <VirtualHost _default_:443> and make the following changes.
Add a line with your server name directy below the ServerAdmin email line. This can be your domain name or IP address:
/etc/apache2/sites-enabled/default
ServerAdmin webmaster@localhost
ServerName mysite.com:443
Find the following two lines, and update the paths to match the locations of the certificate and key we generated earlier. If you purchased a certificate or generated your certificate elsewhere, make sure the paths here match the actual locations of your certificate and key:
SSLCertificateFile /etc/apache2/ssl/apache.crt
SSLCertificateKeyFile /etc/apache2/ssl/apache.key
Once these changes have been made, check that your virtual host configuration file matches the following.
<IfModule mod_ssl.c>
<VirtualHost _default_:443>
ServerAdmin webmaster@localhost
ServerName example.com:443
DocumentRoot /var/www/html
. . .
SSLEngine on
. . .
SSLCertificateFile /etc/apache2/ssl/apache.crt
SSLCertificateKeyFile /etc/apache2/ssl/apache.key
Save and exit the file.
Restart Apache to apply the changes.
sudo service apache2 reload
You can visit your site in a web browser, using HTTPS in the URL (https://site.com) or if not using a DNS entry, use the IP address of the server (eg https://10.10.22.30). Your browser will warn you that the certificate is self-signed. You should be able to view the certificate and confirm that the details match what you entered earlier in this tutorial.